Summary
On November 17th, 2021 Microsoft disclosed the existence of a high severity information disclosure vulnerability impacting Azure Active Directory (Azure AD) that could allow authenticated Azure AD user to escalate their privileges. Azure AD is Microsoft’s Identity and Access Management system used by Azure Cloud and Office 365. The vulnerability, dubbed “CredManifest” (CVE-2021-42306) existed because Azure incorrectly wrote private certificates data in cleartext in Application and Service Principal Manifests. These manifests can be read by any authenticated Azure AD user by default.
Successful exploitation of this vulnerability could have allowed an attacker with access to any account in target’s Azure AD environment to read private certificates from manifests. Attackers could then leverage those certificates to authenticate as the application with the “contributor” role, granting them full access to manage all Azure resources.
Microsoft has since mitigated the vulnerability by restricting access to the “keyCredentials” property in Application and Service Principal manifests as of October 30th, 2021. Restricting access to the property which contains the private certificate data ensures that attackers can no longer access the sensitive data. However, it’s possible that attackers have gathered these credentials prior to Microsoft becoming aware of the issue and thus may still have access to privileged credentials for impacted environments. The Cyber Fusion Center strongly recommends that organizations identify impacted Application registration and Service Principals and rotate those certificates as quickly as possible and investigate Azure AD audit logs for suspicious activity from associated accounts.
For additional details on how to identify impacted App registrations & Service Principals, please review the “solution” section of this advisory.
Affected Azure AD Services
| Azure AD Service | Impacted Scenarios |
| Azure AD Automation with “Run As” accounts enabled | Any Azure AD automation accounts created with “Run As” accounts generated between 10/15/2020 – 10/15/2021 are impacted. Automation accounts created with Managed Identities are not impacted. |
| Azure Migrate service | Azure Migrate appliances registered prior to 11/02/2021 or registered with auto-update disabled are impacted. |
| Azure Site Recovery (ASR) | Users who deployed the preview version of VMware to Azure DR with Azure Site Recovery before 11/01/2021 are impacted. |
| Azure AD Applications and Service Principals | Please review the “solution” section of this advisory to identify impacted Azure AD Apps & Service Principals. |
Solution
Microsoft has update Azure software to mitigate and resolve the issue, however certain Application and Service Principal credentials must be rotated to fully remediate the issue. Please follow the guidance listed in this advisory and Microsoft’s remediation guide to identify credentials that must be rotated.
CFC Releases Free Tool to check for impacted Applications & Accounts
The Cyber Fusion Center has also created a free tool to allow organizations to identify impacted Automation “Run-As” accounts, Application Registrations, and Service Principals. The tool allows Azure AD administrators to easily see impacted credentials that need to be rotated. The free tool is available at the following location:
https://credmanifest.kudelskisecurity.com
Once an organizational administrator has granted read-only content to the tool, organizations will be able to see identify impacted Applications: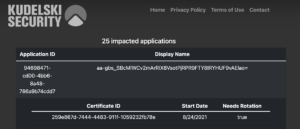
A listing of applications that are impacted and should have their credentials rotated
Manually Identifying Impacted Applications, Service Principals, and Run-As Accounts
Microsoft has enhanced manifests on impacted objects to return new properties that help identify impacted credentials that must be rotated. Organizations can identify impacted Azure AD Aps and Service Principals by looking a property of “hasExtendedValue” within the “keyCredentials” object being set to true.
Below is an example of an *impacted* credential (notice the hasExtendedValue property set to True):
{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#applications(keyCredentials)/$entity",
"keyCredentials": [
{
"customKeyIdentifier": "7A28B6653D0319E69D27E74580E7C91D765AF867",
"endDateTime": "2021-05-21T03:35:32Z",
"keyId": "772faab4-9b59-456e-b73e-baadbfa4b92d",
"startDateTime": "2020-05-21T03:15:32Z",
"type": "AsymmetricX509Cert",
"usage": "Verify",
"key": "MIIDKzCC……",
"displayName": "CN=MyCert",
"hasExtendedValue": True
}
]
}
Free Microsoft Scripts to identify impacted Applications, Service Principals, and Run-As Accounts.
Additionally, Microsoft has made several scripts and automation tooling available to identify and remediate impacted Azure AD App Registrations and Service Principals here:
https://github.com/microsoft/aad-app-credential-tools
What the Cyber Fusion Center is doing
The Cyber Fusion Center is actively working to develop tooling to help clients identify impacted App registrations and Service Principals. The CFC will engage directly with clients who subscribe to CFC services that required Azure AD App Registrations to support data and alert consumption (such as the CFC’s MDR For Endpoint with Microsoft Defender for Endpoint and MDR for Cloud with Azure / Office 365) to identify if they are impacted, and if necessary, rotate credentials.
The Cyber Fusion Center will engage with clients to directly coordinate the rotation of impacted certificates and credentials and ensure no impact to the delivery of your CFC services. Clients working to mitigate impacted Azure AD App registrations should coordinate with the CFC to ensure we can continue to receive critical data required to deliver your services.
Temporary Workarounds and Mitigations
Microsoft has proactively mitigated the issue by limiting access to private certificate data from manifests. This has prevented attackers from gaining access to private certificates since 10/30/2021. However, impacted credentials must still be rotated to ensure attackers who may have exploited this vulnerability prior to mitigation do not retain privileged access to Azure AD environments.
Organizations who identify impacted App registrations and Service Principals should review Azure AD audit logs for sign of abuse of these credentials as soon as possible.
Sources
- https://www.netspi.com/blog/technical/cloud-penetration-testing/azure-cloud-vulnerability-credmanifest/
- https://msrc-blog.microsoft.com/2021/11/17/guidance-for-azure-active-directory-ad-keycredential-property-information-disclosure-in-application-and-service-principal-apis/
- https://github.com/microsoft/aad-app-credential-tools
- https://credmanifest.kudelskisecurity.com


