Despite recent takedowns of multiple CnCs related to dridex, we still see a significant amount of Dridex samples.
To facilitate triage and extraction of IOCs, we developed a configuration extractor that is able to obtain the version and “server list” (CnC) of dridex version 120, 220 and 301.
This tool performs a static analysis by enumerating the sections, trying to deobfuscate and finally decompresses the results with aplib (thanks to @angealbertini for the python implementation of aplib).
To run the script, first you need to clone the github repository and copy the python aplib implementation (you can find the python file for aplib here: https://corkami.googlecode.com/svn-history/r522/trunk/misc/MakePE/examples/packer/aplib.py) in the same folder. Obviously, if the sample is packed you’ll need to unpack it (no need to reconstruct the imports).
See below the output on some samples:
Version 120:
Version 301:
Check out the script here: https://github.com/kudelskisecurity/Dridex-config-extraction
Feel free to contact us for any question.
Happy IOCs extraction!


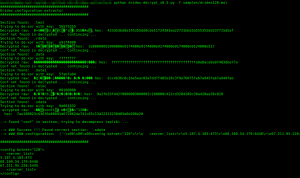

Hi,
Thanks for making this. I’ve installed it on OSX and on linux and can’t get the conf files of the few dridex exes I have. Here is the level of output I’m getting:
Dridex configuration extractor
##########################################
Section found: .text
Trying to de-xor with key: c701f052
Decrypted raw: L?7T7S?R/?iR???v??U??d????_ hex: 4cf037543753b1522fc56952c7f7b476cf00845591e964cfc701a9d9015f
Conf not found in decrypted … continuing …
Section found: .rdata
Trying to de-xor with key: 4ad70100
Decrypted raw: ?~nJ?hrJ? hex: 1c000000b40100007e0000006e0000004ad70100680f0000720f00004ad7
Conf not found in decrypted … continuing …
Section found: .data
Trying to de-xor with key: dc524100
Decrypted raw: ?RA??RA?mV?+1e?;/f? hex: dc52410000000000c0010000dc524100f26d0056a82b3165833b2f66b312
Conf not found in decrypted … continuing …
Section found: .rsrc
Trying to de-xor with key: 00000000
Decrypted raw: 8?X??? hex: 000005000400000038000080050000005800008006000000980000801000
Conf not found in decrypted … continuing …
Then no more. Trying it on this 220 sample:
https://www.virustotal.com/en/file/bbf503d960c62e2aadb5aa270aa05b0f937b28be1b7cca3cad0339fb59273493/analysis/
Any help would be appreciated!
Firstly, thank you, good work!
Secondly, do you have a ‘safe’ link for pefile/itertools/argparse please?
Thanks Chris,
I’m using ubuntu and python-pip for these dependencies.